forexsystem.me
forexsystem.me |
- Trading Forex Sendiri VS Robot VS Copy Trade Untung Mana?
- Guide to Role-Based Access Control
- What Leverage Should I Use in Forex? (Follow This Advice!)
- Biometric Access Control Guide – business.com
- Scammer Exposed! Forex Trading Professor Review 2021
- Brivo Access Control 2021 Costs and Trial Download
- �� CURSO DE FOREX Completo para Principiantes (Curso desde cero) ��Valido 2022 1 de 4
- Honeywell Access Control 2021 Costs and Trial Download
- (TOP 5) Minimalist Trading HACKS To Make You A MASTER Forex & Stock Trader
- IDenticard Access Control 2021 Costs and Free Trial
| Trading Forex Sendiri VS Robot VS Copy Trade Untung Mana? Posted: 29 Oct 2021 03:53 PM PDT Halloween Sale! Buy 1 get 10% off, Buy 2 get 15% Shop Now https://www.dresslily.com/promotion/Halloween-pre.html Hot deals ,ALL $12.99 Hot deals ,ALL $9.99 Hot deals ,ALL $6.99 ------------------------------------ Promo IMLEK dari Octa.id Gunakan kode Promo : LUNAR21 Untuk mendapatkan promo rebate 8$ per lot! Promo berlaku 12 Feb – 12 Maret 2021! Daftar sekarang juga di www.Octa.id Buka akun trading forex di octa.id http://googl.my.id/openocta Sering dengar dan mendapat penawaran robot trading forex? Anda mancing ikan, saldo profit masuk rekening. Sambil menemani anak dapat profit konsisten. Wowwww. Coba kita bahas juga soal copy trade ya! Video ke 15 edukasi forex ini persembahan http://googl.my.id/openocta Vlog 1 : https://youtu.be/XxmozYWU1g0 Vlog 2 : https://youtu.be/j-X1DAQPEjE Vlog 3 : https://www.youtube.com/watch?v=Avh9Ib48bKc&t Vlog 4 : https://youtu.be/V_tbHAmLuj8 Vlog 5 : https://youtu.be/jJGxwre2uMg Vlog 6 : https://youtu.be/cAu5q0A1eT0 Vlog 7 : https://youtu.be/OWJVLJDo9i4 Vlog 8 : https://youtu.be/cgCiGj8aZSc Vlog 9 : https://youtu.be/hCpYvC5-bIM Vlog 10 : https://youtu.be/nafdW0SrKbg Vlog 11: https://youtu.be/nafdW0SrKbg Vlog 12 : https://youtu.be/AF-6oZlxRQ0 Vlog 13 : https://youtu.be/JS7ntsSCxfc Vlog 14 : https://youtu.be/v1cTJMR9zbc Add wa saya di http://googl.my.id/AddWaRyan Semoga terus bermanfaat! Stay tuned! #Forex #Trading #Octa source Click to rate this post! [Total: 0 Average: 0] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Guide to Role-Based Access Control Posted: 29 Oct 2021 03:31 PM PDT Halloween Sale! Buy 1 get 10% off, Buy 2 get 15% Shop Now https://www.dresslily.com/promotion/Halloween-pre.html Hot deals ,ALL $12.99 Hot deals ,ALL $9.99 Hot deals ,ALL $6.99 ------------------------------------ Role-based access control (or RBAC) is a security method in which only authorized individuals who are granted certain permissions can access data that is pertinent to their role in an organization. In this article, we address the inner workings of RBAC and how it can help your company develop a strong cybersecure platform. What is role-based access control?It can be helpful to think of RBAC as representing a set of “keys” that allow individuals – in this case, employees – access to unlock certain “rooms” within your network, or physical areas in your building. As long as the person has the correct key, they can access the needed area within the company or its data. Permissions or security tiers are those “keys” created which then allow users access to that needed data. Users are granted levels of access to a database, data, and related resources based on their role and level of need in the company. RBAC, when it is executed effectively, is a strong defense against cyberbreaches and loss of data, while still allowing for fluid continuity for users in the organization. Read our reviews of the best access control providers offering role based permissions. Understanding how RBAC worksRBAC is rooted in the concept of the specific information an employee needs to access as it pertains to his or her job. If an employee’s role or work does not require that they have access to certain data or a portion of the IT platform, then RBAC access control systems block that employee from those nonessential area(s). For example, you may set a rule that anyone in your finance department cannot access marketing or brand-specific data, and, vice versa, your marketing department cannot access company financials.
Typically (though some companies may construct their RBAC security framework differently), IT security professionals arrange RBAC permissions into one of three systems:
Editor’s note: Looking for the right access control system for your business? Fill out the below questionnaire to have our vendor partners contact you about your needs. What is a user role?A user role relates to the permissions required to perform specific actions or duties (e.g., job-related or project work). Common user roles include:
The benefits of RBACWhether you are a small company seeking an RBAC solution or a large organization with hundreds or thousands of employees, your network security is greatly improved by limiting unnecessary access to data. Additionally, setting up an RBAC system can ensure security and efficiency across departments. Additional benefits include:
How to implement RBAC for your businessThere are many ways to implement an RBAC system; the approach we suggest below is one used by many IT professionals in many industries for both large and small businesses.
RBAC is a needed form of systems management in a time when data – especially proprietary data – is extremely valuable and the threat of cyberbreaches grows daily. RBAC access control systems not only help you maintain complete oversight and security of your network and the data it holds, they are designed to streamline work for your IT staff without impeding your employees’ productivity.
Source link Click to rate this post! [Total: 0 Average: 0] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| What Leverage Should I Use in Forex? (Follow This Advice!) Posted: 29 Oct 2021 02:52 PM PDT Halloween Sale! Buy 1 get 10% off, Buy 2 get 15% Shop Now https://www.dresslily.com/promotion/Halloween-pre.html Hot deals ,ALL $12.99 Hot deals ,ALL $9.99 Hot deals ,ALL $6.99 ------------------------------------ In this Forex trading vlog, I explain what is the best Forex leverage to use depending on your account size. If you’ve been asking yourself “what leverage should I use in Forex trading”, you’ll get the definite answer from this video. Vlog #584
// You Might Also Like… // SOCIAL // TRADING MUST-HAVE RESOURCES // MUSIC // ABOUT ME I blog at www.desiretotrade.com and host the Desire To Trade Podcast. I was fed up with the "fake" millionaire traders and the "get-rich-quick-trading guys". That’s why you can expect more free content from me than what other people charge for! If you truly want to succeed in Forex trading, I believe you need to keep working on yourself so you can improve your strengths, but also your weaknesses. Do not focus solely on what you’re good at. // Disclaimer AFFILIATE LINKS source Click to rate this post! [Total: 0 Average: 0] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Biometric Access Control Guide – business.com Posted: 29 Oct 2021 02:29 PM PDT Halloween Sale! Buy 1 get 10% off, Buy 2 get 15% Shop Now https://www.dresslily.com/promotion/Halloween-pre.html Hot deals ,ALL $12.99 Hot deals ,ALL $9.99 Hot deals ,ALL $6.99 ------------------------------------ Biometrics are biological measurements, physical characteristics or traits that can be used to identify a person and authenticate their identity. Biological biometrics involve genetic and molecular traits, like DNA and blood, while morphological biometrics involve physical traits, such as fingerprint patterns, retinal patterns, facial structure and the pattern of veins in the palm. Behavioral biometrics include a person’s gait, typing pattern and the way they speak, to name a few. What are biometrics?Most small and midsize businesses use a biometrics system based on physical traits. Employees enroll in the system by allowing a scanner component to capture (measure or take images of) whichever type of biometric data the technology uses for the identification and authentication process. Measurements or images are stored as biometric templates, either within the device or on a remote server; this data is usually encrypted for added security. Every biometrics system works by comparing individuals’ templates against “live” information supplied for authorization. For instance, with a fingerprint biometrics system, employees submit to a fingerprint scan so the company can store all authorized personnel’s fingerprints in the system. Then, when an employee comes to work and holds their finger up to the scanner, the system compares the scanned fingerprint with the stored one. Only if a match is established can employees access restricted areas, equipment or files; clock in or out of a time and attendance application; or otherwise “get past” the system. Uses of biometrics in businessAmong the uses of biometrics in business, access control tops the charts. You can install biometric systems to prevent non-employees from entering your premises without checking in first. You can also harness biometric technology to restrict access to equipment (including computers) as well as to corporate networks, digital files and paper records. Biometric systems can also be programmed to allow or deny access based on an individual employee’s role in your organization. For example, you might use a fingerprint scanning system to allow HR managers – but not administrative assistants – access to employee records. Editor’s note: Looking for the right access control system for your business? Fill out the below questionnaire to have our vendor partners contact you about your needs. Jordan Ellington, CEO and founder of SecureReview, said the COVID-19 pandemic and the gig economy have made access control an increasingly important application of biometric systems. “Our current reality is a distributed workforce,” he said. “With people working from home, there are no other absolute methods of verifying user identity on an ongoing basis. When a remote employee or contractor is sitting in front of a computer, facial and other object biometrics ensure that it’s the right contractor or employee. The user cannot hold up a phone or other device to the screen in an attempt to take a picture of a sensitive document.” Biometrics are an equally good fit for time and attendance applications. In this scenario, biometric systems replace traditional time clocks and hardware for stamping timecards. Instead of clocking in or out using these timecards, employees do so by scanning their fingerprint or palm or “showing” their face to a facial recognition system. This prevents employees from engaging in “buddy punching,” or clocking in or out for each other when they arrive late or leave early. Pros of biometricsIt is important to weigh the pros and cons of biometrics and biometric systems before implementing the technology. Advantages of using the best biometric access control systems include the following. Enhanced securityUnlike keycards, key fobs and passwords, people’s biometric traits cannot be lost or stolen, which makes biometric systems a more secure option than their non-biometric counterparts. Additionally, while biometric systems are not entirely foolproof (see below), the likelihood of someone “spoofing” them is minimal. “Should someone be successful in gaining access to biometric data, it will take them quite some time to replicate that data into a usable format,” said Pieter Vanlperen, founder and managing partner of PWV Consultants. “This makes it a deterrent for threat actors, as they do not want to waste time.” Biometric systems provide even more security and better access control when combined with other identification and authentication methods. For instance, fingerprint scans or facial recognition technology can be used to confirm (or deny) that a person who scans an ID badge is really who they claim to be. Convenience for employees and employersBiometric technology is more convenient for employees to use because they do not have to waste time looking for what they need (e.g., a keycard or fob) or remember their password to get through the system. Additionally, biometric systems authenticate and identify people faster than conventional methods of authentication. The convenience of biometrics extends to employers. For example, you are not stuck chasing replacements for lost keycards, key fobs and identification cards. Biometric systems also provide authentic attendance data, so you or your HR personnel need not “browse through heaps of attendance sheets to calculate leaves, late sign-ins or overtime for individual employees,” said Robin Antill, founder and CEO of 1st Choice Leisure Buildings. Potential cost savingsThe cost to replace lost keycards, fobs and other physical access tokens can add up quickly. This doesn’t even include the cost of time spent arranging replacements or resetting passwords for employees. While biometric systems can be costly to buy and install, keep in mind that the price of data breach recovery is often much higher.
Cons of biometricsOn the flip side, here are the disadvantages of biometrics. Physical changes can interfere with accuracy.Biometrics are not infallible. While the data stored on a person’s biometrics never change, people’s physical attributes sometimes do. “The authentication system only identifies traits that were registered and fails to identify the user if their physical traits change in even the most insignificant way,” Antill said. “In such circumstances, the system needs to be altered to grant access to the allowed user, which can be inconvenient.” Antill offered several examples of situations where traits may change, including new tattoos on hands, burned or damaged fingers, retina transplants, and the addition or elimination of eyeglasses. Not all biometric systems are suitable for every application.Environmental and other factors can impact whether a certain type of biometric system will work for your business. For instance, a facial recognition system may not be the best choice if your employees wear masks all day, and fingerprint recognition or palm vein technology may be an impractical option for employees whose jobs involve carrying items from place to place (e.g., in a warehouse). Resetting biometric systems can be problematic.When your entire biometrics system needs to be reset, be prepared for a heavy lift. “One of the biggest disadvantages of biometrics is that biometric data cannot be changed or reset,” said Julien Raby, CEO and founder of Thermo Gears. “If a password is stolen from a database, a new password can be created. But if a biometric characteristic is stolen from a database, a new biometric characteristic cannot be easily issued.” The initial investment could be too high for small businesses.As mentioned above, cost savings is one of the potential advantages of biometrics. However, biometric system hardware, setup and integration require a significant upfront investment that may be difficult for small businesses to bear. Given the multiple uses of biometrics and the various pros and cons of biometric systems, small and midsize businesses have a lot to think about before rolling out biometric technology. Regardless, building a wide base of knowledge about the technology will help you make an informed decision and increase your potential for return on investment in the long run. What are the different types of biometrics and biometrics systems?The following types of biometrics and biometric systems use physiological characteristics:
There are also biometrics and biometric systems that use these behavioral characteristics:
Which biometric systems are commonly used for access control?Businesses typically choose from these four types of biometrics for access control: FingerprintAdvantages While the price of fingerprint-scanning systems can vary depending on the type of scanner, their suitability for mass production makes them less expensive than other options, according to Varnas. The use of fingerprint scanning on mobile phones means most people are familiar with it, making things easier for businesses that choose fingerprint biometric systems. Disadvantages Fingerprints are more vulnerable to wear and damage than any other biometric. The accuracy of fingerprint scanners may be compromised by cuts, abrasions and scars on the fingers. Another downside is that fingerprints can be collected from surfaces and forged in a few ways, such as 3D printing, unless the fingerprint scanner has built-in technology to discern whether fingerprints are being presented live. Additionally, fingerprint systems are not contactless; users must place their finger on a scanner for reading during authentication. Consequently, they are less sanitary – and, given the COVID-19 pandemic, possibly less desirable – than other types of biometrics and biometric systems. Facial recognitionAdvantages Facial recognition systems are easy to use because enrolled individuals just show their faces to be identified. “Facial [recognition] isn’t expensive to add to existing access control systems, and in many cases, it’s coming almost for free, with good cameras becoming pervasive and facial algorithms getting better at off-angle, off-lighting recognition,” said Steve Humphries, CEO of Identiv. “We don’t think there will be a move away from fingerprint; this will be additive, either as a lower-friction option, new installation or multi-biofactor.” Disadvantages Facial recognition technology can capture facial images from afar. This may lead to privacy and legal risks, except in situations in which the technology is used on personal devices. In addition, because facial recognition measures fewer data points than other types of biometrics, there are more inaccurate results with this technology than with other types of biometric systems. Changes in users’ appearance – like growing or shaving off facial hair, or removing or putting on glasses or makeup – contribute to the likelihood of false negatives. Iris scanAdvantages Iris (retinal) scanners produce biometric IDs by using infrared light and high-resolution cameras to capture the detailed pattern within the iris. This pattern does not change throughout a person’s life, so the accuracy of iris-scanning systems in identifying people does not change as they age. The retina has a significantly detailed pattern, so iris scanners capture many data points, which yield a high degree of accuracy. Disadvantages Iris scanners can obtain images from many feet away. This capability may expose your business to the same risks as facial recognition technology but on a smaller scale, experts from Keyo said. Palm veinAdvantages Palm vein technology maps the palm’s unique vein pattern by using infrared light. Proponents of palm vein technology said it is the most secure option, in part because the vein pattern of the palm is not readily visible to anyone, making it difficult for someone to create a replica that would “fool” the scanner. Because palm vein technology captures a larger surface of the body – and, consequently, more data points – than other types of biometrics and biometrics applications, it offers greater accuracy, as well as fewer false negatives and positives, than other types of biometrics, some sources said. Disadvantages The weather can affect biometric results. Specifically, cold weather can reduce blood flow and reduce the accuracy of palm vein biometrics. What should you look for when choosing which biometrics to utilize in your system?Consider these factors when choosing which biometric to measure:
What to consider when choosing a biometrics systemThere are several factors you should take into account when choosing a biometric system:
What are the benefits of using biometrics for authorization and access control?The goal of biometrics is to ensure that those accessing the location, device or network are who they claim to be, Varnas said. The problem with traditional authentication, through means such as a password or key fob, is that it doesn’t matter who is using them. If the password is correct or the fob is in the person’s hand, they can gain access. “With biometrics, you’re far more likely to be able to ensure that you’re only allowing the intended party to access [whatever you’re trying to protect],” Varnas said. All types of biometrics offer three main benefits over other authentication and verification methods: SecurityBiometrics verify someone’s identity using their unique biological traits, so it is more difficult for another person to steal them outright than to get their hands on a physical access token, like a key card, or misappropriate a password. Additionally, some facial recognition systems have built-in testing mechanisms to ensure that the biometric data is coming from a real human being rather than, for example, a forged composite replica or an image that has been downloaded from social media. The end result is enhanced access control. ConvenienceWith biometric access control, authorized users need nothing other than themselves to be granted access. This means that neither you nor your employees need to worry about resetting forgotten passwords or PINs, or replacing lost keys, barcodes or chip-based identification cards. Employees also appreciate not having to fumble for physical access tokens or recall passwords as they attempt to gain access. Moreover, some sources said manual verification checks can take less time than verification checks performed using biometric identifiers – again, streamlining the verification and access control process. Cost savingsReplacing key cards, fobs and other physical access solutions can be costly. According to a study by Tile, each lost ID card can cost up to $50, with the average cost per replacement card now averaging $22. It may not sound like a lot, but it adds up over time, especially when you consider the time spent on the replacement process. What’s more, the cost of recovering from a data breach caused by unauthorized access to sensitive data can outweigh the cost of implementing biometric authentication and access control systems. What are the drawbacks of biometrics and biometric systems?Biometrics and biometric systems come with some limitations:
Source link Click to rate this post! [Total: 0 Average: 0] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Scammer Exposed! Forex Trading Professor Review 2021 Posted: 29 Oct 2021 01:51 PM PDT Halloween Sale! Buy 1 get 10% off, Buy 2 get 15% Shop Now https://www.dresslily.com/promotion/Halloween-pre.html Hot deals ,ALL $12.99 Hot deals ,ALL $9.99 Hot deals ,ALL $6.99 ------------------------------------ In this video, we reviewed Forex Trading Professor forex signal services and discussed everything need to know about this service before using this service. Recommended Brokers links:- Watch other provider reviews: Disclaimer: Trading involves the possibility of financial loss. Only trade with money that you are prepared to lose, you must recognize that for factors outside your control you may lose all of the money in your trading account. Many forex brokers also hold you liable for losses that exceed your trading capital. So you may stand to lose more money than is in your account. https://trustedforexreviews.com takes no responsibility for loss incurred as a result of our trading signals. By signing up as a member you acknowledge that we are not providing financial advice and that you are making the decision to copy our trades on your own account. We have no knowledge of the level of money you are trading with or the level of risk you are taking with each trade. You must make your own financial decisions, we take no responsibility for money made or lost as a result of our signals or advice on forex related products on this website source Click to rate this post! [Total: 0 Average: 0] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
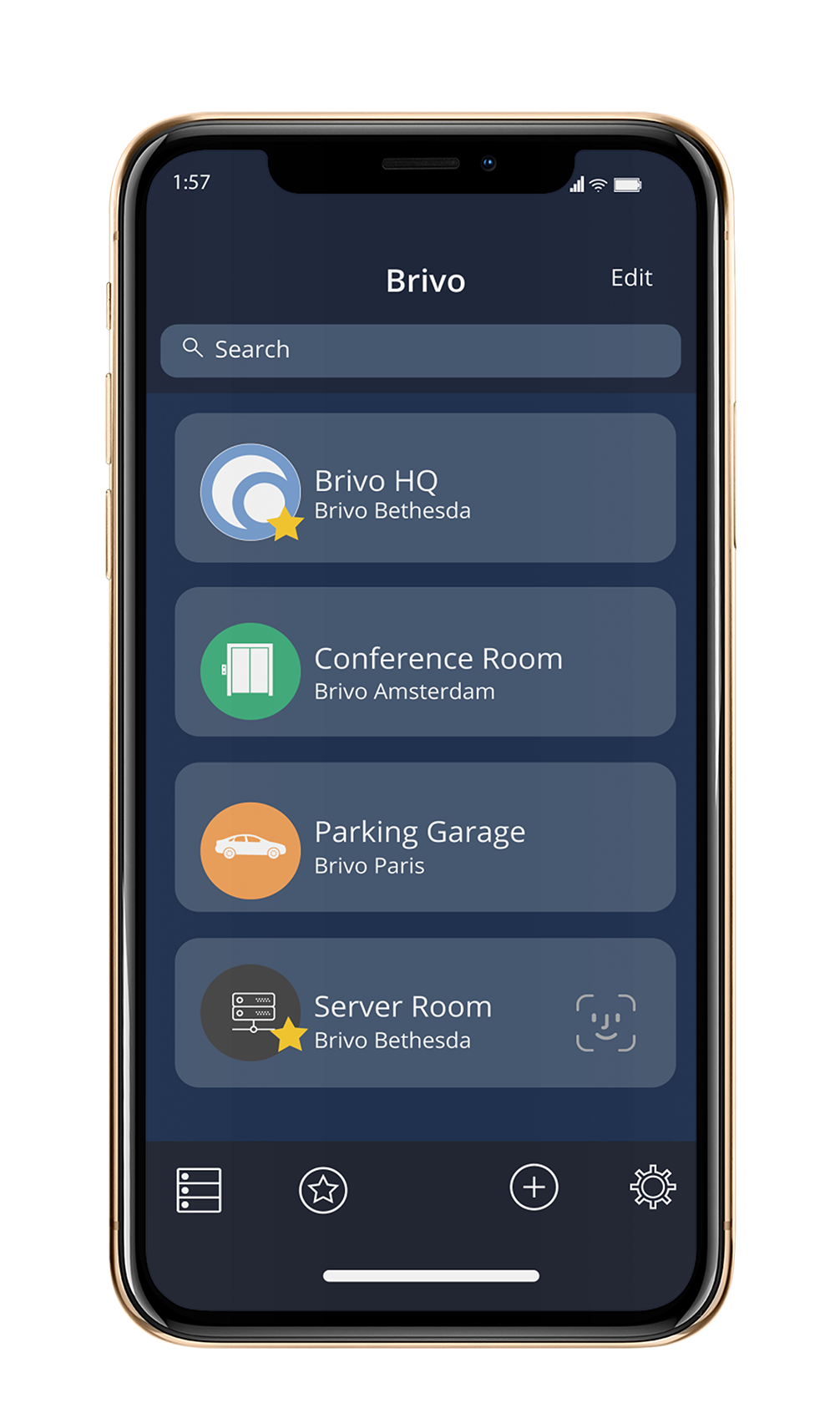
| Brivo Access Control 2021 Costs and Trial Download Posted: 29 Oct 2021 01:27 PM PDT Halloween Sale! Buy 1 get 10% off, Buy 2 get 15% Shop Now https://www.dresslily.com/promotion/Halloween-pre.html Hot deals ,ALL $12.99 Hot deals ,ALL $9.99 Hot deals ,ALL $6.99 ------------------------------------ Brivo’s access control features don’t include the access cards common among cloud-based solutions. Instead, Brivo users’ mobile devices function as access cards. That isn’t the only innovation that Brivo brings to access control, though. Learn more below, and read our full Brivo review. What Is Brivo?Brivo is a security company that introduced cloud-based access control to the world in 2002. This development arrived three years after Brivo’s 1999 founding in Bethesda, Maryland. As of June 2015, Dean Drako, who founded the video surveillance company Eagle Eye Networks, owns Brivo. As such, Brivo’s cloud-based access control has become more integrative with video surveillance systems in recent years. Brivo remains independent of Eagle Eye Networks. Does Brivo Have a Free Trial?Rather than offering a free trial, Brivo allows interested customers to request a demo of its access control software. Brivo does not explicitly state how long this demo lasts before you must pay, so we recommend you contact Brivo for more information. Brivo PricingBrivo pricing varies based on the results of a security assessment that Brivo will conduct for your company. However, if you opt for Brivo Complete, you will pay a flat $99 activation fee.
Brivo Access Control ProductsWhen you choose Brivo, you have four options: Brivo StandardBrivo Standard provides your company with basic access control features. You can use it to secure your facilities and keep your team safe. If needed, you can also purchase Brivo’s identity connector, API integrations and single sign-on (SSO) tools. Notably, Brivo Standard does not include door readers, as it is intended for small-scale, software-only use. Brivo Standard includes the following functions:
Brivo ProfessionalWith Brivo Professional, you’ll get real-time monitoring, automation, extensive integrations and thorough analytics. It includes everything in Brivo Standard plus these features:
Brivo EnterpriseBrivo Enterprise ups your access control system to include real-time data insights. It includes everything in Brivo Professional plus these features:
To make the above information easier to understand, we’ve compared Brivo Standard, Professional and Enterprise in the below table:
Brivo CompleteBrivo introduced its Complete platform in 2020. Brivo Complete combines Brivo Onair (which you’ll also use to log in to Brivo Standard, Professional or Enterprise) with video cameras, Brivo control panels and Brivo Readers. Although Brivo Complete includes far more hardware than Brivo’s other products, its functional differences from these products are minimal. Its main distinguishing factor is its subscription model, which Brivo says is rare among access control systems. Brivo intends for this system to eliminate upfront cash barriers to purchases.
Brivo access control products overview Brivo Payment OptionsBrivo accepts credit card payments, electronic funds transfers or checks. You can also sign up for Brivo’s payment programs to keep your access control costs within your budget. Best Features of BrivoThese are some of Brivo’s best features across its four access control systems:
 Source: Brivo
SummaryBrivo is a user-friendly access control system with easy setup and just the right number of features. We recommend it for any small business that needs comprehensive access control with as few upfront costs, installation requirements and hardware devices as possible. If you’re looking for an access control setup with biometric features, consider companies like Honeywell, or IDenticard if you need a more advanced setup. Brivo FAQsHow much does Brivo cost?Brivo’s costs are based on the security analysis the company conducts for your business. If you choose Brivo Complete, you’ll pay an additional $99 flat installation fee. What is Brivo Onair?Brivo Onair is the interface through which you access your cloud-based Brivo system. It is not a stand-alone Brivo product. How are Brivo mobile passes used?To use a Brivo mobile pass, open the Brivo app, then choose the location and door you want to access. Then, hold down the center unlock button. When your screen turns green, you’ll have access to the door.
Source link Click to rate this post! [Total: 0 Average: 0] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| �� CURSO DE FOREX Completo para Principiantes (Curso desde cero) ��Valido 2022 1 de 4 Posted: 29 Oct 2021 12:48 PM PDT Halloween Sale! Buy 1 get 10% off, Buy 2 get 15% Shop Now https://www.dresslily.com/promotion/Halloween-pre.html Hot deals ,ALL $12.99 Hot deals ,ALL $9.99 Hot deals ,ALL $6.99 ------------------------------------  Curso de Forex para Principiantes (Curso Completo), aprende las bases del trading y prepárate para el análisis técnico sin tener experiencia. Curso de Forex para Principiantes (Curso Completo), aprende las bases del trading y prepárate para el análisis técnico sin tener experiencia. Ver Temario Ver Temario  * Cuenta demo con $10,000 para practicar: https://divisas4x.com/go/youbroker/ Índice del Curso de Forex: 00:00 Intro
Curso de Forex “Análisis Técnico” (2 de 4): https://youtu.be/Kw-PYV62nDs Gracias a este curso, muchas personas han tenido un mejor acercamiento al mercado más grande de mundo y ha servido de inspiración a traders y youtubers para realizar videos sobre trading. En este curso aprendes Como Invertir Dinero en Forex, el Curso de Forex ha sido el primero en español para principiantes y avanzados. El Curso de forex y Analisis Tecnico es Valido para: Mercado de Divisas Forex Curso de Inversion #cursoforex #forex #forexprincipiantes source Click to rate this post! [Total: 0 Average: 0] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Honeywell Access Control 2021 Costs and Trial Download Posted: 29 Oct 2021 12:27 PM PDT Halloween Sale! Buy 1 get 10% off, Buy 2 get 15% Shop Now https://www.dresslily.com/promotion/Halloween-pre.html Hot deals ,ALL $12.99 Hot deals ,ALL $9.99 Hot deals ,ALL $6.99 ------------------------------------
Among access control companies, Honeywell is perhaps the closest thing to a household name. The brand is known for its industrial and manufacturing arm, but it manufactures powerful access control tools as well. That said, users new to access control systems may find the technology challenging to adopt and understand, read our full Honeywell review. Does Honeywell Have a Free Trial?Honeywell does not have a free trial. However, since you must buy Honeywell’s access control products from a third-party retailer rather than from Honeywell directly, you may find free trials depending on which retailer you choose.
Honeywell PricingHoneywell does not list prices on its website. As we say in our Honeywell review, you need to contact Honeywell for a quote. An alternative way to obtain prices for Honeywell’s access control software is to create an account with one of the sellers listed on each product’s Honeywell page. Upon creating an account, you can request a quote from the seller. Prices will vary based on which product you buy. Below, we’ve broken down the basics of each product. Honeywell Access Control ProductsHoneywell offers two access control software platforms: WIN-PAK;Honeywell’s WIN-PAK software interface can oversee your company’s intrusion detection, access control and video surveillance. You can access it from any web browser, thus facilitating remote access control. If you buy WIN-PAK when your company is small, you can easily scale it as your company grows from one facility to many. That’s because WIN-PAK has no maximum number of users or locations. It also accommodates as many as 40 recorders and 2,560 cameras. Additionally, WIN-PAK integrates extensively with point-of-sale (POS), visitor management, biometric and HR platforms. It also comes with an API that your software development team can use to create and customize integrations specific to your company. 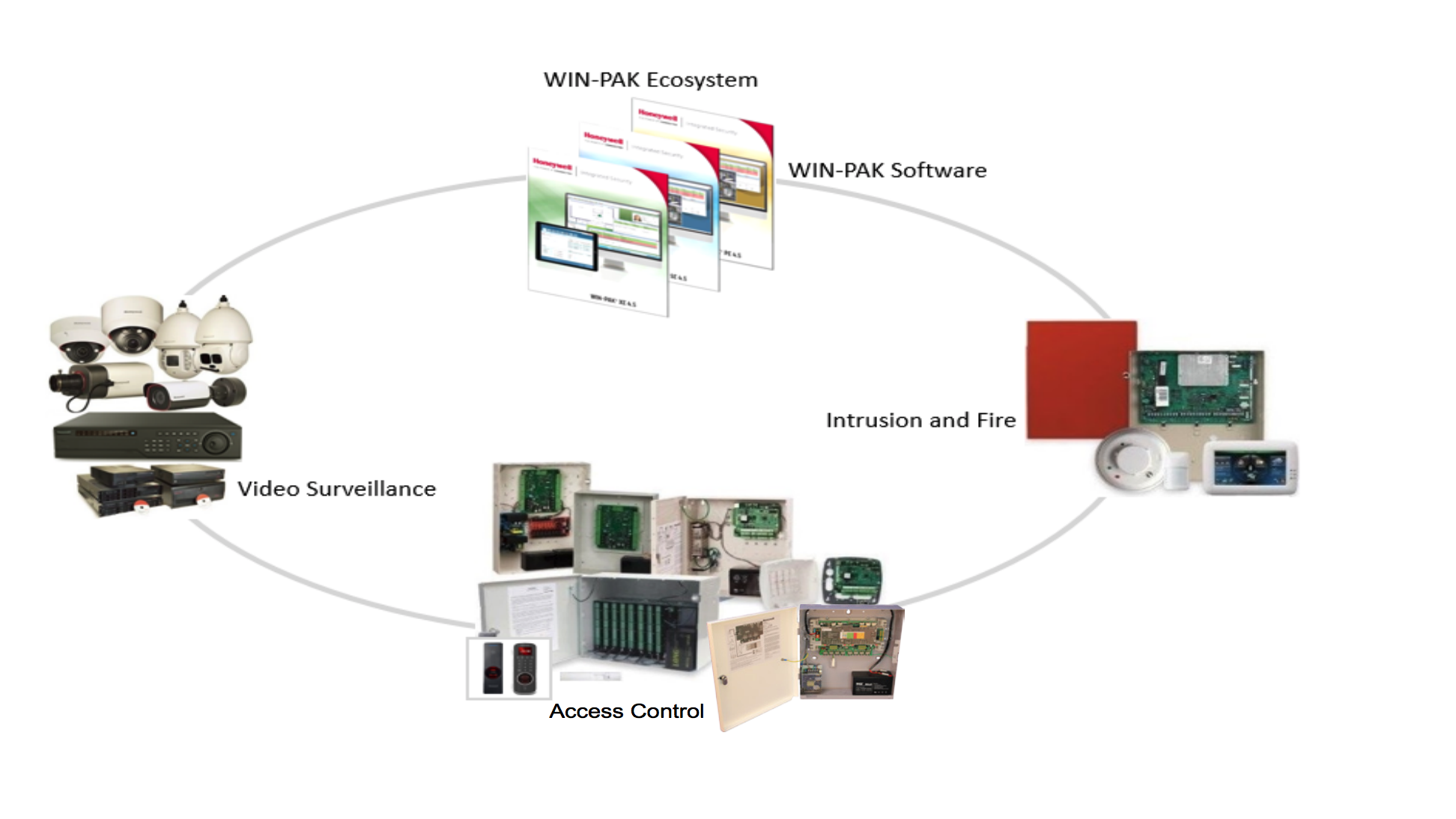 Source: Honeywell WIN-PAK CS 4.7WIN-PAK CS 4.7 is a cloud-based version of WIN-PAK. With WIN-PAK CS 4.7, you can control several accounts from one system whether you’re on mobile or desktop. According to Honeywell, WIN-PAK CS eliminates several costs compared to WIN-PAK. These costs pertain to maintaining your database, updating your operating system, and managing your servers and workstations. Additionally, using WIN-PAK CS 4.7, you can access day-to-day functions, view door statuses, schedule and create reports, lock and unlock doors, and locate access events. You can also locate employees, generate muster reports and find lost or unused access cards. Honeywell Payment OptionsBecause you will be purchasing Honeywell products from a third-party vendor rather than directly from Honeywell, you may encounter different payment terms depending on the vendor. Best Features of HoneywellThe best features of Honeywell’s two access control software platforms include the following:
Perhaps given this overwhelming number of features, you’re confused about which feature corresponds to which WIN-PAK software. The table below should clarify:
SummaryHoneywell’s WIN-PAK and WIN-PAK CS 4.7 systems offer comprehensive access control features for businesses of all sizes. However, given both tools’ overwhelming number of features, you face a steep learning curve. As such, if you need a scalable access control platform, then Honeywell might be worth it. Otherwise, you may prefer simpler solutions like SimpliSafe or Kisi. Honeywell FAQsWhat does Honeywell make?Honeywell makes access control software and hardware, though it is arguably better known for its consumer home products (e.g., thermostats) than its business solutions. What are Honeywell’s access control products?Honeywell primary access control products are its WIN-PAK and WIN-PAK CS software. How can I buy Honeywell access control products?To buy Honeywell access control products, you must visit a Honeywell third-party trusted seller website, create an account and then make your purchase.
Source link Click to rate this post! [Total: 0 Average: 0] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (TOP 5) Minimalist Trading HACKS To Make You A MASTER Forex & Stock Trader Posted: 29 Oct 2021 11:46 AM PDT Halloween Sale! Buy 1 get 10% off, Buy 2 get 15% Shop Now https://www.dresslily.com/promotion/Halloween-pre.html Hot deals ,ALL $12.99 Hot deals ,ALL $9.99 Hot deals ,ALL $6.99 ------------------------------------ Discover a minimalist approach to Forex and stock trading, with 5 rules to make you a better trader. In this video you'll learn: • What is minimalism in trading and how you can keep your trading simple and effective • The steps you need to make to improve your trading, to 'out smart' the rest of traders • Why is important to ditch all the unnecessary trading indicators from your charts • Why you shouldn't over complicate support & resistance levels and trend lines • How to reduce the market noise by using higher time frames • Why you must use price action as your main technical analysis method • How to develop a trading routine and respect it
Trade with confidence with our RECOMMENDED online stock trading TOOLS, best online Forex trading platforms and Metatrader platforms, stock trading simulators, stock screeners, penny stock screeners, stock trading picks, investment portfolio tools (and discover our online stock trading sites and stock firms recommendations)
Check out our Playlists | Learn to trade Fx – Online Fx Trading | How To Trade Stocks And Shares | Stock Trading Techniques | Trading For Dummies |Trend Trading Forex | MT4 trading systems
Best Forex & Stock Trading Platform Software We Use: https://www.tradingview.com/
RISK DISCLAIMER: Please be advised that I am not telling anyone how to spend or invest their money. Take all of my videos as my own opinion, as entertainment, and at your own risk. I assume no responsibility or liability for any errors or omissions in the content of this channel. This content is for educational purposes only, and is not tax, legal, financial or professional advice. Any action you take on the information in this video is strictly at your own risk. We therefore recommend that you contact a personal financial advisor before carrying out specific transactions and investments. There is a very high degree of risk involved in trading. Past results are not indicative of future returns. TheSecretMindset.com and all individuals affiliated with this channel assume no responsibilities for your trading and investment results. AFFILIATE DISCLOSURE: Please note that some of the links above are affiliate links, and at no additional cost to you, we will earn a commission if you decide to make a purchase after clicking through the link. We only promote those products or services that we have investigated and truly feel deliver value to you. source Click to rate this post! [Total: 0 Average: 0] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| IDenticard Access Control 2021 Costs and Free Trial Posted: 29 Oct 2021 11:23 AM PDT Halloween Sale! Buy 1 get 10% off, Buy 2 get 15% Shop Now https://www.dresslily.com/promotion/Halloween-pre.html Hot deals ,ALL $12.99 Hot deals ,ALL $9.99 Hot deals ,ALL $6.99 ------------------------------------
Although IDenticard’s name may suggest that ID cards are its bread and butter, IDenticard can do far more than identify people. Through its PremiSys technology, IDenticard also offers comprehensive access control features for businesses of all sizes. Learn more below, and read our full IDenticard review. What Is IDenticard?IDenticard was founded in 1970 as a photo ID company. Since then, it has grown into a lauded identification and access control provider owned by the workplace safety behemoth Brady Corporation. Because Brady Corporation owns IDenticard, all IDenticard hardware and software are produced in-house rather than by a third party. IDenticard’s primary offices are in Pennsylvania, Massachusetts, and Ontario; however, its customer base spans the entire world. IDenticard has regional offices throughout the U.S. to give customers local expertise. IDenticard’s customers number in the tens of thousands and span sectors that include education, manufacturing, government and more. Many of its clients are Fortune 500 companies and household names such as 3M, Target and Coca-Cola. Does IDenticard Have a Free Trial?IDenticard does not explicitly state that its PremiSys technology includes a free trial. However, all IDenticard orders have a 30-day full-refund return window, and orders over $99 include free shipping.
If you are interested in a PremiSys access control system, we recommend inquiring with IDenticard about the possibility of a free trial. IDenticard Pricing and TiersIDenticard’s access control prices depend on which of its four access control systems you purchase for your small business. The first of these three systems are tools known as PremiSys. Each version of PremiSys is a different tier that IDenticard offers for a different price. All three PremiSys tiers mostly overlap in terms of functionality, though they vary in a small number of ways. PremiSys isn’t IDenticard’s only useful access control tool. You may also find IDenticard’s Rack Armor tool useful if your company’s servers are on-site. We explain more about PremiSys and Rack Armor below. PremiSys LTYou can use PremiSys LT for up to eight doors. You get one user interface, and you’ll be able to use the IDenticard mobile app. Given these parameters, IDenticard recommends PremiSys LT for smaller businesses. PremiSysYou can use PremiSys to secure up to 40 doors. You’ll get up to three user interfaces, and you have the same mobile app access as with PremiSys LT. Unlike PremiSys LT, PremiSys comes with ID badge creation. IDenticard recommends this tier for large companies with many workstation clients. PremiSys ProYou can use PremiSys Pro on an unlimited number of doors. You get an unlimited number of user interfaces, standard mobile app access and ID badge creation. IDenticard is best suited for enterprise businesses. If you think that the three PremiSys tiers don’t differ much, you’re right. That’s because, unlike many top access control companies, IDenticard doesn’t segment most of its key features by tier or business size. We’ll explain those features later. Rack ArmorIn addition to PremiSys, IDenticard offers a platform called Rack Armor intended for guarding access to server rooms. Larger organizations that have on-site servers instead of using cloud-based apps or web hosting may feel that Rack Armor maximizes their security. That said, most small businesses use some form of off-site servers. As such, Rack Armor may not be necessary for your company. 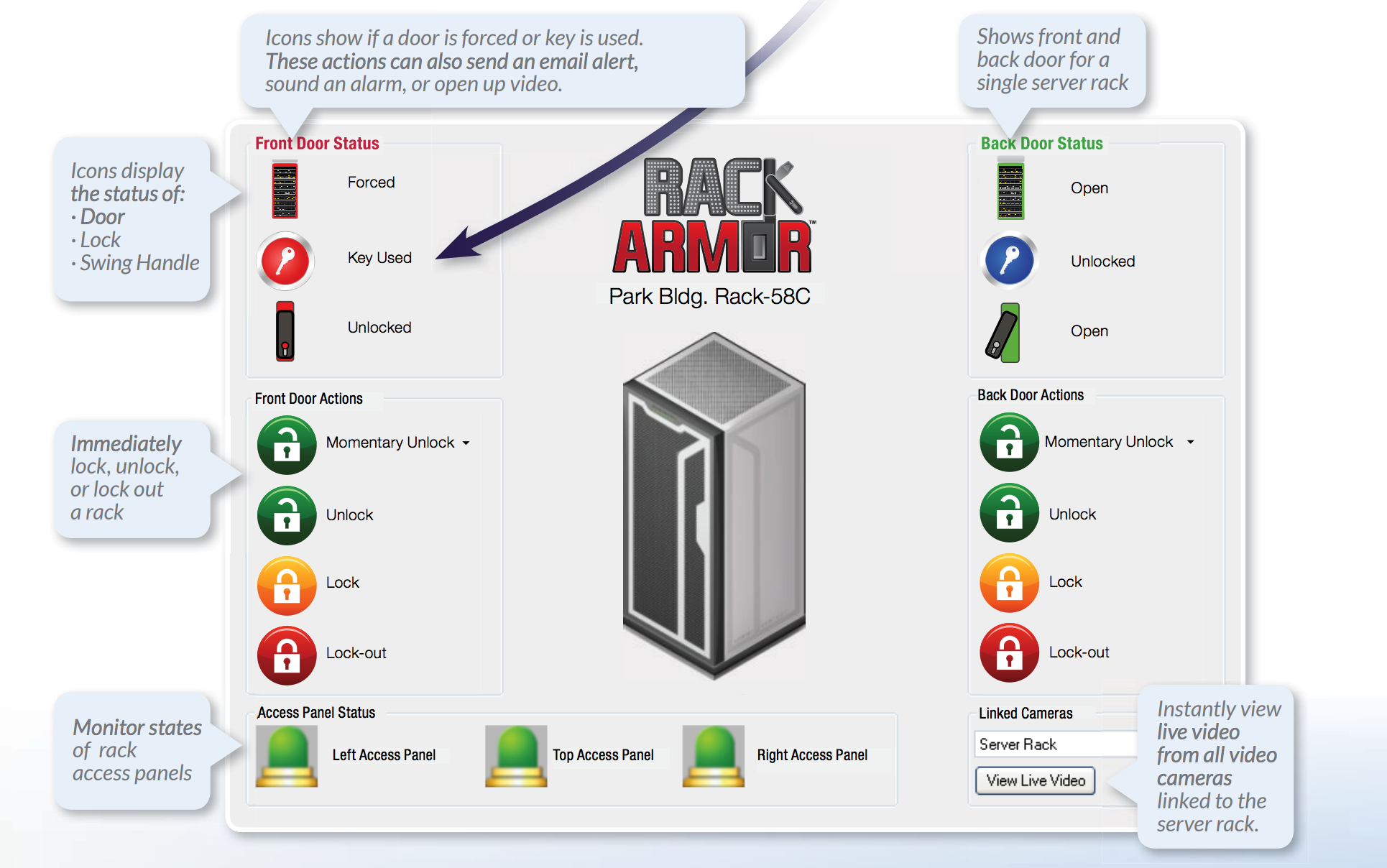 Source: IDenticard IDenticard Payment OptionsWhen you first purchase your IDenticard access control tools, cash on delivery (COD) is an option. Should you go this route, IDenticard accepts money orders or certified checks. If you order additional tools after your first purchase, you can pay with a check if IDenticard’s credit department preapproves the transaction. Additionally, IDenticard accepts Visa, MasterCard and American Express cards. Best Features of IDenticardThe best features of IDenticard’s PremiSys access control technology include the following:
SummaryIDenticard’s PremiSys access control system provides extensive features for companies of all sizes. Since IDenticard offers most PremiSys features for all three access control tiers, PremiSys can easily scale with your company. Much like Honeywell, IDenticard offers biometric options. If you’re looking for a simpler solution, consider SimpliSafe or Kisi. As your company grows, you may find PremiSys’ higher-level features more important. However, because you’ll have these features at the outset no matter your business size, we recommend IDenticard and PremiSys for all companies. Its versatility can meet many of your security needs. IDenticard FAQsWhat is IDenticard?IDenticard is a company that creates ID cards and offers access control technology to companies of all stripes. What is PremiSys?PremiSys is IDenticard’s access control technology. It is available in three tiers that mostly overlap but have minor differences. What is Rack Armor?Rack Armor is IDenticard’s access control platform for server rooms. It includes features optimal for guarding server access from anyone who should not have those privileges.
Source link Click to rate this post! [Total: 0 Average: 0] |
| You are subscribed to email updates from Forex System. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |


 Did You Know: With a larger teams managing role based permissions allows for different levels of access to your property or data. If you have a property with a less access points consider a simpler system like
Did You Know: With a larger teams managing role based permissions allows for different levels of access to your property or data. If you have a property with a less access points consider a simpler system like 
 FREE Case Study “Quitting Your Job To Finally Trade Full-Time”: https://desiretotrade.co/case-study
FREE Case Study “Quitting Your Job To Finally Trade Full-Time”: https://desiretotrade.co/case-study Bottom Line: Biometric security won’t make sense for every business looking to secure their physical location, and online data. Consider looking for a
Bottom Line: Biometric security won’t make sense for every business looking to secure their physical location, and online data. Consider looking for a  Tip: If you’re in need of a biometric solution read our reviews of
Tip: If you’re in need of a biometric solution read our reviews of  Day Finance Ltd: https://www.youtube.com/watch?v=LSLo5b4oJQY
Day Finance Ltd: https://www.youtube.com/watch?v=LSLo5b4oJQY FYI: You can always add more Brivo mobile passes than your plan initially includes, but you’ll pay extra for each additional pass.
FYI: You can always add more Brivo mobile passes than your plan initially includes, but you’ll pay extra for each additional pass. Gratis cuenta para practicar SIN Riesgo: https://divisas4x.com/go/ytbroker/
Gratis cuenta para practicar SIN Riesgo: https://divisas4x.com/go/ytbroker/
 Ready for some TRADING and INVESTING action?
Ready for some TRADING and INVESTING action?
Comments